What Is the MD5 Hashing Algorithm & How Does It Work?
In the realm of cryptography and digital security, hashing algorithms play a crucial role in ensuring data integrity and providing a means of verification. Among these algorithms, MD5 (Message Digest algorithm 5) has been a significant player since its introduction in 1991. Despite its age and known vulnerabilities, MD5 remains relevant in various applications, making it an important subject for anyone involved in computer science, cybersecurity, or digital forensics.
The MD5 hashing algorithm, designed by Ronald Rivest to replace an earlier hash function MD4, is a widely used hash function that produces a 128-bit hash value. It was originally designed for use as a cryptographic hash function, although it has since been found to suffer from extensive vulnerabilities. Despite these weaknesses, MD5 continues to be widely used for non-cryptographic purposes such as checksum verification of downloaded files and storage of password hashes. This article delves into the intricacies of the MD5 algorithm, exploring its structure, functionality, applications, and the reasons behind its continued relevance in certain contexts.
The Fundamentals of Hashing Algorithms
Before diving into the specifics of MD5, it's essential to understand the basic concept of hashing algorithms. A hash function is a mathematical algorithm that takes an input (or 'message') and returns a fixed-size string of bytes. The output, called the 'hash value' or simply 'hash', is typically a hexadecimal number. The key properties of a good hash function include:
- Determinism: The same input should always produce the same hash output.
- Quick computation: The hash function should be capable of returning the hash value quickly for any given input.
- Pre-image resistance: It should be computationally infeasible to reverse the hash function, i.e., to find an input that produces a specific hash value.
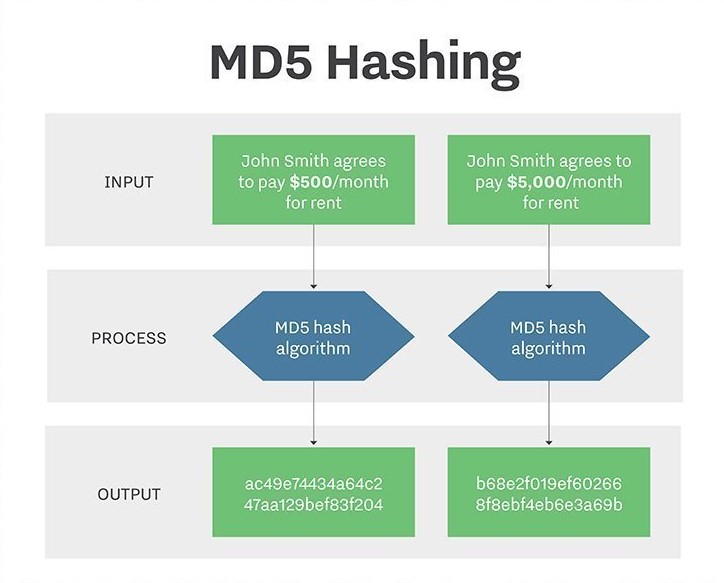
- Small changes in input yield large changes in output: A slight modification in the input should result in a significantly different hash value.
- Collision resistance: It should be extremely difficult to find two different inputs that produce the same hash output.
Hashing algorithms are used in various applications, including digital signatures, password storage, file integrity verification, and data structures like hash tables. The choice of a hashing algorithm depends on the specific requirements of the application, balancing factors such as security, speed, and output size.
The Structure of MD5
The MD5 algorithm takes as input a message of arbitrary length and produces as output a 128-bit "fingerprint" or "message digest" of the input. The MD5 algorithm is designed to be quite fast on 32-bit machines. In addition, the MD5 algorithm does not require any large substitution tables; the algorithm can be coded quite compactly.
The MD5 algorithm consists of five steps:
- Append Padding Bits
- Append Length
- Initialize MD Buffer
- Process Message in 16-Word Blocks
- Output
Each of these steps plays a crucial role in the overall function of the algorithm. Let's explore each step in detail to understand how MD5 transforms an input message into a fixed-size hash output.
Step 1: Append Padding Bits
The first step in the MD5 algorithm is to pad the message so that its length in bits is congruent to 448, modulo 512. In other words, the padded message must be 64 bits less than a multiple of 512 bits in length. Padding is always performed, even if the length of the message is already congruent to 448, modulo 512.
Padding is done as follows: a single "1" bit is appended to the message, and then "0" bits are appended so that the length in bits of the padded message becomes congruent to 448, modulo 512. In all, at least one bit and at most 512 bits are appended.
Step 2: Append Length
A 64-bit representation of the length of the message before the padding bits were added is appended to the result of the previous step. If the length of the message is greater than 2^64, only the low-order 64 bits of the length are used.
These two steps (1 and 2) serve to make the message length an exact multiple of 512 bits, which is essential for the subsequent processing steps.
Step 3: Initialize MD Buffer
A four-word buffer (A, B, C, D) is used to compute the message digest. Here each of A, B, C, D is a 32-bit register. These registers are initialized to the following values in hexadecimal (low-order bytes first):
- word A: 01 23 45 67
- word B: 89 ab cd ef
- word C: fe dc ba 98
- word D: 76 54 32 10
These values are hard-coded into the algorithm and serve as the starting point for the hash computation.
Step 4: Process Message in 16-Word Blocks
The heart of the algorithm is the compression function that operates on each 512-bit block of the padded message. This step involves four rounds of processing, where each round consists of 16 similar operations based on a non-linear function F, modular addition, and left rotation.
MD5 uses four different functions (F, G, H, I), one for each round:
- F(X,Y,Z) = (X AND Y) OR ((NOT X) AND Z)
- G(X,Y,Z) = (X AND Z) OR (Y AND (NOT Z))
- H(X,Y,Z) = X XOR Y XOR Z
- I(X,Y,Z) = Y XOR (X OR (NOT Z))
Each round consists of 16 operations, and each operation performs a nonlinear function on three of A, B, C, and D. Then it adds that result to the fourth variable, a subblock of the text and a constant. The result is then rotated a variable amount and added to one of A, B, C, or D.
The exact details of these operations involve complex bit manipulations and are typically implemented in low-level programming languages for efficiency.
Step 5: Output
After all the 512-bit blocks have been processed, the output from the last stage is the 128-bit message digest. The contents of buffer words A, B, C, D are converted from little-endian format to big-endian format and concatenated to form the final MD5 hash value.
The Mathematics Behind MD5
The MD5 algorithm relies heavily on bitwise operations and modular arithmetic. The core of the algorithm involves manipulating 32-bit words using operations such as AND, OR, NOT, and XOR, as well as addition modulo 2^32 and bit rotation.
One of the key mathematical properties of MD5 is its use of non-linear functions in each round. These functions are designed to have certain properties that make the hash function resistant to various types of cryptographic attacks. For example, the functions are chosen so that if the input bits are altered slightly, each bit of the output is affected with a probability of 0.5.
The algorithm also makes use of a table of pseudorandom numbers. This table is produced from the sine function, adding an element of trigonometry to the mix. Each round uses 16 operations, for a total of 64 operations in the main loop of the algorithm.
Applications of MD5
Despite its known vulnerabilities, MD5 continues to find use in various non-cryptographic applications. Some common uses include:
- Checksum verification: MD5 is often used to verify the integrity of files after download or transfer. By comparing the MD5 hash of the downloaded file with the hash provided by the source, users can quickly check if the file has been corrupted during transmission.
- File identification: In large databases or file systems, MD5 hashes can be used as a quick way to identify duplicate files without comparing the entire contents.
- Password hashing: Although no longer recommended for secure applications, some legacy systems still use MD5 for storing password hashes.
- Digital signatures: In some applications, MD5 is still used as part of digital signature schemes, although more secure alternatives are strongly recommended for new implementations.
- Random number generation: The MD5 algorithm can be used as part of pseudo-random number generation processes in certain applications.
Vulnerabilities and Limitations of MD5
While MD5 was once considered cryptographically secure, it has been shown to suffer from extensive vulnerabilities. The most significant of these include:
- Collision vulnerability: In 2004, it was shown that it is computationally feasible to find two different inputs that produce the same MD5 hash. This severely compromises the collision resistance property that is crucial for many cryptographic applications.
- Preimage vulnerability: While not as severe as the collision vulnerability, techniques have been developed that can find preimages for MD5 faster than brute force attacks, though still not fast enough for practical use.
- Length extension vulnerability: MD5 suffers from a length extension vulnerability, where an attacker who knows the hash of an unknown message can append to the message and produce a valid hash for the new message without knowing the original message.
Due to these vulnerabilities, MD5 is no longer considered suitable for security-critical applications, especially those related to digital signatures or certificate generation.
Alternatives to MD5
Given the known vulnerabilities of MD5, several more secure alternatives have been developed and are widely used:
- SHA-256: Part of the SHA-2 family, SHA-256 produces a 256-bit hash and is widely used in security applications and protocols.
- SHA-3: The newest member of the Secure Hash Algorithm family, SHA-3 was selected through a public competition and offers improved security features.
- BLAKE2: A high-speed hash function that can be used as a replacement for MD5 in most applications, offering improved security and performance.
- bcrypt: Specifically designed for password hashing, bcrypt incorporates a salt and is deliberately slow to compute, making it resistant to brute-force attacks.
When choosing an alternative to MD5, it's important to consider the specific requirements of the application, including security needs, performance constraints, and compatibility with existing systems.
Conclusion
The MD5 hashing algorithm, despite its age and known vulnerabilities, remains an important topic in the field of computer science and cryptography. Its structure and functionality provide a foundation for understanding more advanced hashing algorithms, and its continued use in certain non-security-critical applications makes it relevant for many practitioners.
Understanding MD5 involves delving into the intricacies of bitwise operations, modular arithmetic, and the principles of cryptographic hash functions. While MD5 is no longer recommended for security-sensitive applications due to its vulnerabilities, studying its design and the attacks against it provides valuable insights into the evolution of hash functions and the ongoing challenge of balancing security, efficiency, and ease of implementation in cryptographic algorithms.